
+- Curl Global Community (https://communities.curl.com)
+-- Forum: Tutorials (https://communities.curl.com/forumdisplay.php?fid=3)
+--- Forum: Public Training (https://communities.curl.com/forumdisplay.php?fid=4)
+---- Forum: Curl IDE Made Easy (https://communities.curl.com/forumdisplay.php?fid=6)
+----- Forum: Try 0: Installing the Curl Development Environment (https://communities.curl.com/forumdisplay.php?fid=8)
+----- Thread: Page 2: Setting up the privilege settings (/showthread.php?tid=39)
Page 2: Setting up the privilege settings - ashimo - 06-16-2011
 Assign Special Privileges to the Working Folder
Assign Special Privileges to the Working Folder The working folder
The working folderWith Curl, we can create applets that can be executed over a network, but during development it is convenient to perform execution/debugging on a local machine. In this manual, we will be using the 'Curl' directory on the C drive to hold applets under development. The following steps configure Curl to grant privileges to this location. You can, of course, use any directory in any location.
1. As shown in Figure 0-8, click start and select All Programs > Curl RTE > Curl Control Panel. The screen shown in Figure 0-9 appears.
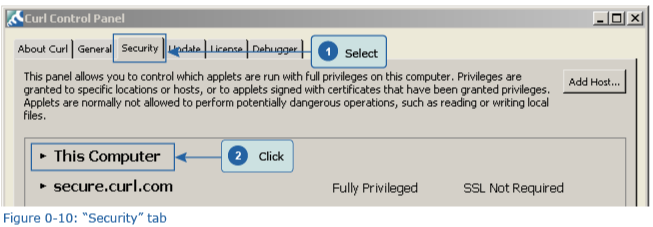
2. Click the “Security Options” tab, and then click “This Computer”.
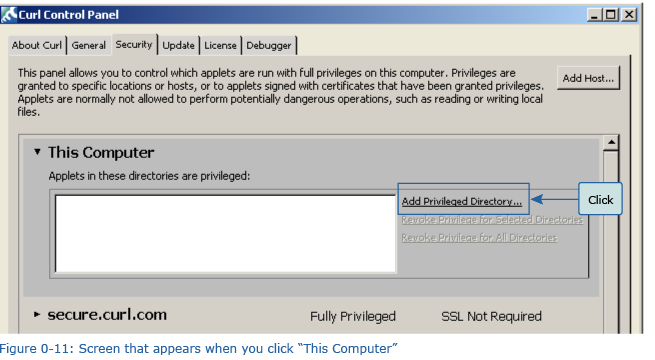
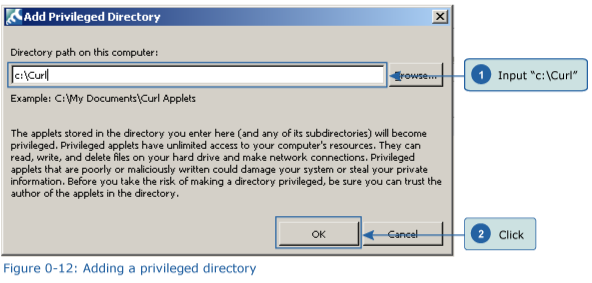
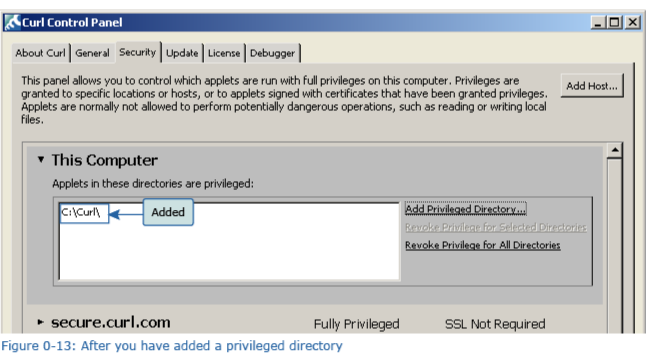
3. After the screen switches to that shown in Figure 0-11, click “Add Privileged Directory.” The dialog box shown in Figure 0-12 appears. Input “c:\Curl”, and then click "OK". Once the privileged directory has been added to this computer, the screen shown in Figure 0-13 appears.
 Security and Privileges
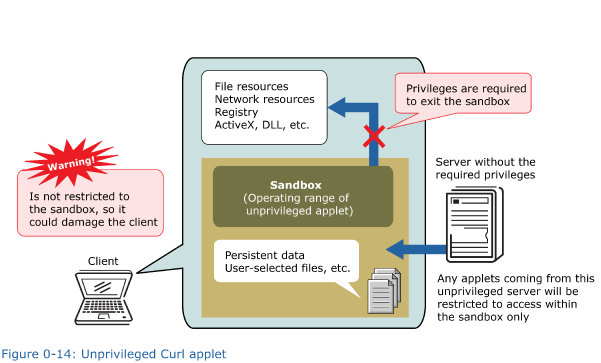
Security and PrivilegesUsually, Curl applets are stored on a Web server. From the server, users can download the applets, and then execute them on their PCs. If we were to allow applets unlimited access to resources such as the files stored on the hard disk of a user’s PC, or the registry, then it would be possible for malicious applets to steal or even destroy data. Curl RTE has been designed to protect a user’s PC from this kind of danger, and limits the range of client resources that can be accessed by a Curl applet. We call this range, in which access is possible, the “sandbox.”
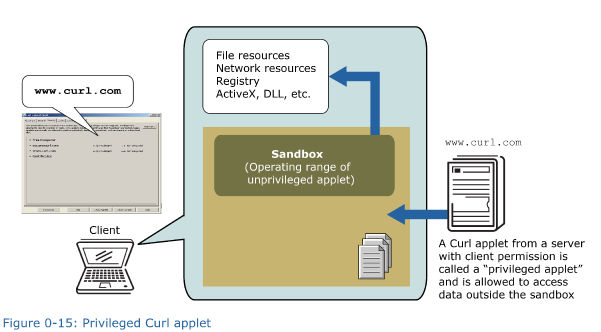
When the user knows that an applet can be trusted, he or she can change the settings to lift this restriction from Curl RTE. Applets that are not subject to this restriction are called “privileged applets” and have full access to the client’s resources.
The examples given in this manual assume that applications are stored and executed locally, and not served from a Web server. If applets or other resources, such as images, are stored on a Web server or other location, privileges are still required to execute the Curl applet. With Curl, you can assign privileges to other locations using the same methods as explained in STEP 4 in which you would specify the directory containing the applet.